Threat Modeling
Why Wildcard?
The goal of threat modeling is to select the proper controls to address identified threats. Without appropriate threat modeling, security controls and procedures can be ineffective because they do not address the unique threats facing the organization. The Wildcard approach to threat modeling uncovers any technological, process, or organizational gaps in security controls and allows for enhanced risk management practices that align with the mission of your organization.
We are a privately-owned company that is unencumbered by any third parties. This allows us to react nimbly and provide exactly what our customers need when they need it. Wildcard employs domain experts who have provided secure, robust services for large government agencies, utility companies, small businesses, and universities. Our breadth of experience gives us the insight to understand the range of threats facing your organization and the challenges that must be overcome to mitigate them. Where other firms may take knowledge with them, we leave it with you, empowering your organization and people.
Our Services:
- Threat Modeling
- Penetration Testing
- HIPAA Compliance
- PCI Compliance
- Web Application Assessment
- Code Review
- Information Security Training
- Virtual Chief Information Security Officer
- Wireless Assessment
Overview of Threat Modeling
Developing a threat model is the process of mapping the specific, unique threats to your organization and the methods used to attack any information technology asset or collection of assets. The two primary goals of threat modeling are:
- Provide a clear perspective of assets, threats, and possible attacks to facilitate discussions regarding risk management decisions and practices.
- Discover and evaluate gaps in security controls at the application, system, infrastructure, and enterprise levels.
The concept of conducting threat modeling exercises has been around for as long as distributed information systems have been used to process data. Since the inception of the idea there have been various methodologies that solve a specific problem but may not scale to an enterprise level, are not applicable outside of the Software Development Lifecycle (SDLC), or are not repeatable.
The Wildcard Threat Model reflects the different threats faced by different technology teams from IT to software development. Our model can be tailored to individual stakeholders throughout an organization to reflect their areas of responsibility. This capability allows for the entire organization to work in concert to evaluate the threats to the enterprise and develop strategies to address those risks.
Asset Analysis
Threat models must begin with the Crown Jewel Analysis, or the identification of the most critical assets. Your organization's mission is dependent on the confidentiality, integrity, and availability of these assets. These business and security assets must be protected and have their risk exposure limited. By understanding what is critical to your organization, we can identify the dependencies and the threats you face.
Define the Attack Surface
The next step is to create a comprehensive map of the components of the application, system, or environment that contain, communicate with, or otherwise provide some form of access to the assets. The attack surface will help define the boundaries, scope, roles, and responsibilities in the threat model.
Mapping Threats and Attacks
Threat mapping begins with determining the sources of attack and their motivation. Disgruntled employees, state actors, and random script kiddies are all examples of potential threats to your system. Each threat actor can have different skill sets, resources, and objectives and must be accounted for when developing the model.
Wildcard is uniquely positioned to provide a comprehensive list of threats because we are an incident-response service provider. We have observed threat actors in real-time across multiple industries. We know how the adversary operates and the current techniques used in the field.
Threat Analysis
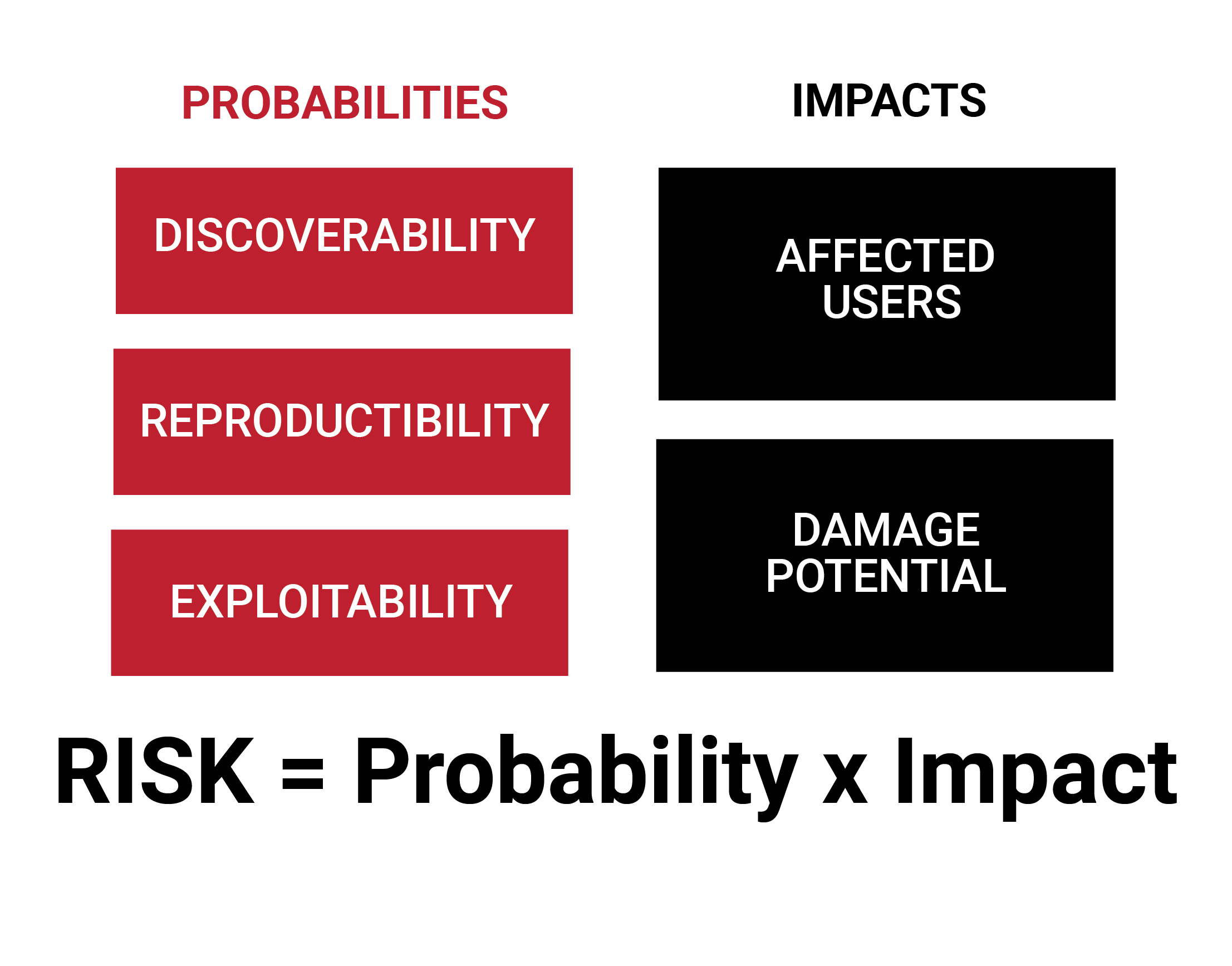
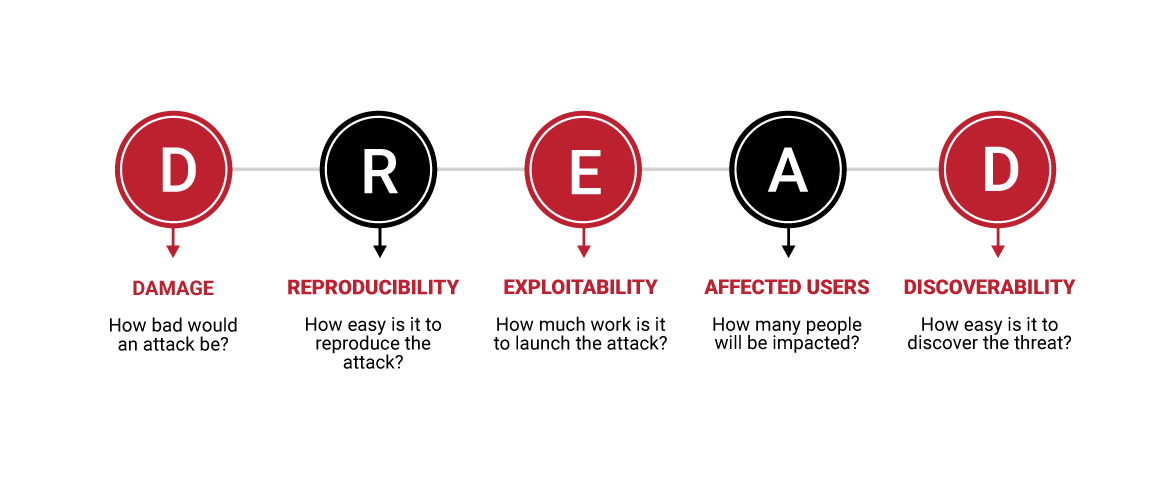
Next is the analysis phase, the results of which allow your organization to make decisions that maximize the effectiveness of the security devices (such as firewalls, intrusion detection systems, and spam filters) and procedures that mitigate threats and attacks. The DREAD Method is a simple, extensible model that allows for comparing and ranking risks in an easy-to-understand manner.
The values that are derived by DREAD allow your organization to focus its energy on the most vulnerable portion of your information systems and prioritize your efforts on implementing controls to reduce risk.