Fight the Phish

When you use it on a daily basis, it’s easy to forget that email is an unsecured medium of communication. According to the Verizon 2019 Data Breach Investigations Report, they found that for the median company, 94% of detected malware was delivered by email. This goes to show the importance of understanding phishing to promote cybersecurity best practices. If we can eliminate the number of successful phishing attacks, this high rate of malware delivery by email will not affect our personal or work systems.
This week to promote Cybersecurity Awareness Month, we are focusing on the theme: Fight the Phish. Understanding how to spot phishing attacks can be vital to the protection of your organization and sensitive information. Remember, it’s up to you to think before you click or give up information.
Fight the Phish
Phishing can be defined as the sending of emails to make it appear to be from a reputable source with the goal of influencing or gaining sensitive information. Phishing is a form of social engineering that works to gain an emotional response from the recipient in order to execute a malicious attack. We are going to work through some main sections of emails and explain the red flags to look for that give up an email as the malicious phishing attack it is.
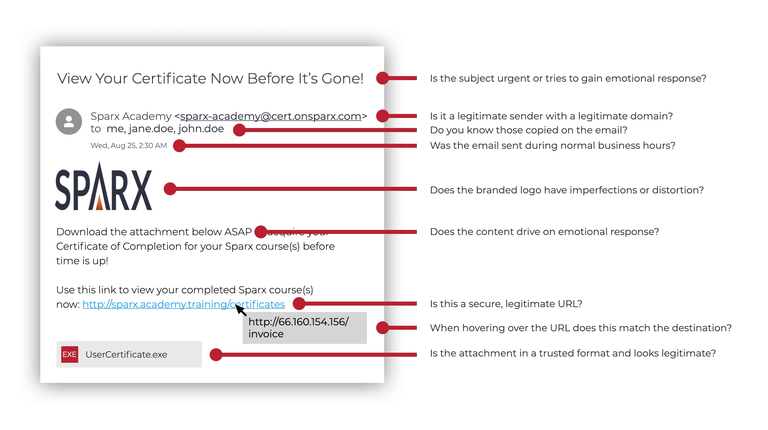
1. Subject Line
Starting at the top of an email, one of the first things we look at is the subject line. We use subject lines to tell the recipient the overarching theme of that email. It’s often used as a tool by marketers to provoke interest to get a reader to open the email and then click through to another website.
Hackers use subject lines in a phishing email as a tool to provoke an emotional response or urgency to the recipient. Lines that warn of time-sensitive content are a common indicator of a phishing email. Subject lines like these can focus on an important organization or personal factors such as financial status. These topics could also revolve around current events such as COVID-19 or economic concerns.
2. From Line
If you know what to look for, the from line can be one of the classic indicators of a phishing email. Most phishing emails will imitate a legitimate business, organization, or person you may know. Take a closer look at the email address and verify that this is the same email address if you have communicated with them previously.
Some hackers will only change a few characters to look the same at first glance. Check to see if the domain is legitimate. Hackers also may add a word before or after the organization's name. If you see any suspicious signs in the from line, you could contact that organization or person directly and verify that this is a legitimate email address for their communications.
3. To Line
Depending on the type of phishing attack, the to line might also have a few indicators you can pick up on. Hackers may send an email to multiple individuals; check their email addresses for legitimacy. Ask yourself if these are people you know and have communicated with before. If not, this could indicate that a phishing attack was sent to various email accounts.
4. Time Stamp
If you log in to your email account first thing in the morning, the timestamps could show suspicious activity. Emails sent outside of normal business hours could lead to deducting the email as a phishing attack.
5. Logos
Take time to analyze any logos, headers, or any other branded graphics that are included in the email. We discussed how most phishing emails impersonate legitimate organizations or businesses, so graphics that are low quality, distorted, or warped could be an indicator of a phishing attack. Most legitimate companies have strict guidelines about branded graphic usage, including dimensions, colors, and quality. Hackers don't have access to these brand guidelines but will try to make the emails look as similar as possible to trick you at first glance.
6. Content
Content is the key when it comes to determining an email from a phishing attack. The first thing to reiterate is that a basic email is an unsecured form of communication. No legitimate business, organization, or individual will ask you to send sensitive information, such as credit card numbers, social security numbers, or other personally identifying information via email. This practice would not put them in compliance with many industry standards such as PCI DSS or HIPAA.
Knowing that phishing attacks will be requesting this type of information or other confidential data, it might seem simple to hit the report button and contact your IT department right away. But hackers understand that they need to execute their messaging in a way that will make you willing to give up the information as soon as you read the email; this is called emotional response. Emotional response is the messaging that makes you act fast to not think about the legitimacy of the request. Types of emotional response attempt to:
- Cause stress
- Illicit fear
- Give rewards
- Utilize authority
- Appeal to your desire to help others
- Create a sense of urgency
When you receive emails that make you feel these emotions, they are a strong indication that you have received a phishing email. Whether the email is from your boss or your banking institution, contacting a trusted source such as their real phone number can verify the legitimacy of the request. Even if the email is from an individual requesting personal or sensitive information, contact them directly to find another secure form of communication to meet compliance requirements and protect your data.
7. Links
It is crucial to scrutinize the links in an email. Certain links will take you to fraudulent or unsecured websites and even execute malicious downloads to your system. Never click on links provided in emails. Instead, open your web browser and type in the website you need to go to directly. This ensures that you are accessing a legitimate website to check your account status and verify the information in the email received is legitimate.
It is important to also never click on shortened URLs, as these can hide the actual domain location. If you know the destination it wants to take you to, use the above method and go to your website browser and type it in manually. You can also hover your mouse over the URL, and the email client will show you where the link will take you. Other resources include website services to validate the source of a tiny URL.
8. Attachments
The last section of an email to be wary of is attachments. If there is an attachment included in an email, verify the document name matches the content of the email. You should never download attachments from people or organizations you don’t know. If you know the sender, verify that the sender is who they say they are before downloading.
Some of the most common file types to avoid include .exe, .rar, and .zip files. This doesn’t mean that these are automatically dangerous, but it’s important to think before you download them to your systems. If any of your downloads ask you to enable macros or programmatic capabilities, refrain from doing so, as these can execute potentially malicious code.
Reporting the Phish
If you have identified several of these sections with suspicious attributes, it’s time to report the email. Verify the identity of the sender or the legitimacy of the organization with a trusted source. It’s better to be wrong in your accusation than to be compromised by an attack. Let your IT department know about your findings, and they can help you verify if the email was a phishing attack. It’s important to install email filters and anti-virus software onto your systems to help reduce phishing attempts.
If you believe that your systems have been compromised by a phishing attack, report this to your management and IT department right away. If you have given up any sensitive information, be sure to report this as well. Notify the correct organizations if applicable, such as your financial institution if you gave up sensitive financial information. Change your passwords on any other accounts necessary and watch for signs of identity theft or financial fraud.
Phishing is an attack that feeds off of human error. You are the last defense between hackers and your sensitive information. Remember to look for any of these suspicious warning signs early on. Think before you click and remember: Do Your Part. #BeCyberSmart