A Holistic View of Security
When people are asked about "security", a multitude of images roll through people's heads. Everything from armed guards and electric fences, to absurdly long and complex passwords that your boss tells you must be changed every 2 weeks. The truth of the matter is, all of those visualizations are right on one level or another. Yet, to think of just one of them as being the pinnacle of security, whereby, if you have at least have one then you'll be safe, would be flat out wrong.
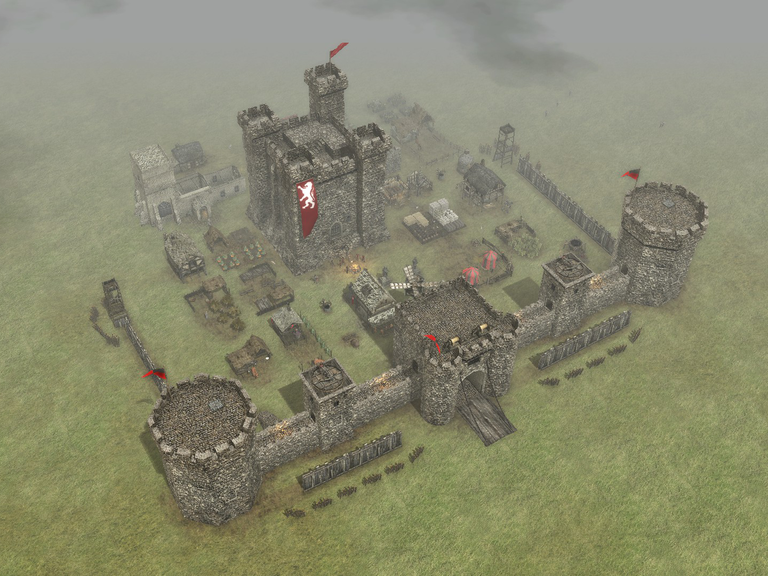
In the following picture I've used the video game Stronghold 3 by FireFly Studios to create a depiction of what this kind of thinking would produce if all aspects of security were translated into the terms of purely physical security. As you can see, the front side of the castle is heavily fortified. Attacks from this direction are well defended against. However, as attacks are launched more to the sides, the castles defenses quickly diminish. In fact, the rear of the castle has been left completely undefended, leaving the castle extremely vulnerable to any attacks from that direction. In this exaggerated example, it is clearly visible that the castle's defenses do not provide holistic security and is actually not very secure.
In the past, their are books that will tell you to approach security by evaluating the risks, rank them, and then start addressing each risk beginning with the highest priority. I'm here to tell you that this notion of priority is flawed and there are many reasons why.
First and foremost is that lists tend to give a ranking of importance to the items included in the list. This type of ranking leads to a sense of urgency to take care of the first few items and a sense of complacency about addressing the items lower on the list. Once the first few items are taken care of people tend to rationalize that they need not worry about the rest. But when it comes to security, all list items are equally important, no matter the order they are placed in. As we already saw with the castle example, your security must be complete to be truly effective, so the list cannot remain only half complete.
Second is the fact that establishing such a priority means that you have a deep understanding of both the magnitude of effect and probability of occurrence for any given event. While mountains of statistics could be accumulated to obtain a better establishment of priority, it's normally not necessary because everything that presents itself as a threat should actually be evaluated and addressed. About the only worthiness of establishing the priority would be when it comes to budgeting. But, more on that later.
Now, the final reason I'll give about why a priority list is not appropriate is that many aspects of security should be deployed in controlled stages from the ground up. Because of dependencies, even though a particular threat may be very real and viable, its mitigation may require multiple other components to be in place. It would be akin to saying that a house built in Seattle, WA (one of the rainiest cities in the U.S) must have an excellent roof and gutter system to handle all the expected rainfall. As water damage can be quite sever and the frequency of rainfall is very high, the general contractor decides to build a roof as his top priority before even digging the foundation for the house. While such a thought is comical and brings back memories of Saturday morning cartoons with impossible feats accomplished that defy the laws of physics, trying to establish security policies out of order can be just as absurd.
So, where does one start then when establishing security policies and practices?
Check out this article on Building a World Class Security Operations Center.
Lead Image courtesy of Ryan Lea
Contact us today if you have questions or would like more information!
(715) 869-3440
or fill out our easy Contact Form!